Enterprise Security Solutions
Advanced Network Security
Solutions for Enterprises
800+
Happy Clients
1900+
Projects Completed
30+
Business Partners
6
Countries
Solutions Provided by Us
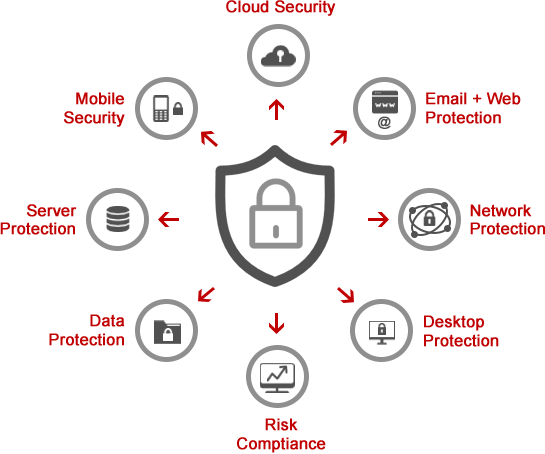
EJAF provides advanced network security solutions for enterprises. We are trying our best to be one of the top security solution integrators by working on expertise and by obtaining an experimental experience. EJAF has a partnership with highly qualified, skilled engineers and sellers from leading industries that have experience in handling organized enforced networks and infrastructures.

Advanced Persistent Threat (APT) Defense Framework
The advanced persistent threat, which is also termed a targeted threat, is a type of attack following the footsteps of a unique and legible model to become successful. Advanced Persistent-Threat is not just a mere piece of malware but also a technology used in different operations. And when it comes to the model of APT, it provides enterprise security solutions. It is a fully secure framework that also has intelligence sharing to see known and unknown threats. The APT fabric consists of many different components, including entryways, terminations points, and sandboxing used to encounter the terrors beyond the spectrum of Information technology. The model of threat makes sure that the attacks are decreased, and the firm becomes stronger.
Network & Application Security
The Web applications ensure the security and privacy of all three layers of a website: the website, web server, and the database server. Centralize web applications, terror-free firms, customized applications services are provided by Web application Firewalls(WAF), which is the foremost enterprise security solutions. Moreover, by using different schemes, WAF protects from dangers like [SQL] injections, hacking of cookies, scamming, and further possible web attacks.
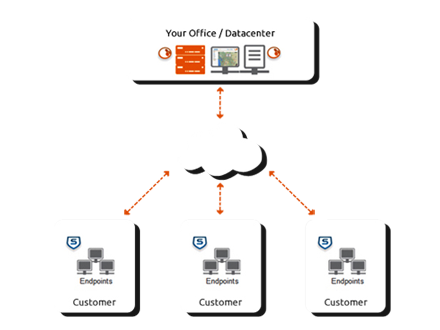

Application Delivery Controllers
Firms using advanced applications like Microsoft, IBM, Oracle, SAP, or other famous sellers are required to deliver continuous accessibility, smooth and easy access even from different locations, and have increased network security for firms. If you have difficulty in delivering this quality, then the best solution is an application delivery controller. It provides the capability to handle a load and accessibility and security to all the internet-based applications. The propelled application conveyance controllers offer basic server farm capacities, such as layers ranging from four to seven burden adjusting, application speeding up, proactive application well-being checks, security socket layers off-loading, and DDOS assurance, and [DNS] firewalls.
Cutting edge Firewalls
This cutting edge firewall is used to handle networks and internet traffic. It is done by using the specific application. They are also used in the detection of application-specific attacks, thereby decreasing it. It can be either hardware-based or software-based with specific policies and a mixture of protocols and the port that damages the seventh layer. Many characteristics are offered by cutting edge firewalls, including Stateful investigation, application’s understanding, knowledge about the user, Intrusion Protection System, multi-purpose modes, and capacity to use the latest updates from insight resources.

Security & Vulnerability Assessment
Powerlessness evaluation is an inside review of an association’s system and framework security, the consequences of which demonstrate the classification, accessibility, and respectability of the system parts. Weakness Assessment can likewise be named as the procedure followed to distinguish insufficiently made sure about PCs or potentially arranges. Evaluations, likewise, by and large, incorporate numerous methodologies for organizing and applying extra security activities for fixing and protecting frameworks from dangers. Ordinary weakness appraisals make a preemptive spotlight on by and large data security and help recognize likely adventures before programmers discover them. The powerlessness evaluations help disentangle [PCIDSS], [SOX], and [HIPAA] consistency or decreases related expenses.
Patch Management
Missing security refreshes is one of the main danger vectors misused by malware. Patch management provides the enterprise security solution by fixing the board arrangement examines associated endpoints and servers to discover missing patches on OS and outsider applications. This will also help diminish conveyance time for basic and highly risked patches. Moreover, it gives you a perceived ability on the status of current consistency levels against driving industry benchmarks. It gives you broad reports on the most helpless frameworks and in general perspective on the earth.


Ultimate Benefits Of Malware Protection
Malware is a compact of malicious-programming intended to get entrance, steal the information, and harm PC without bringing in a notice of holder. Many different sorts of malware are there, including infections, Worms, dim products, spy products, and any pass-code that has a bad impact on PC. The Protection of Malware arrangement guarantees consistent safety for actions that are done by clients accessing any app at any gadget, and wherever including protective assurance at odds with infections, Trojans, worms, spyware, emancipate product, and the latest variations that develop normally. Associated danger safeguard conveys quick reaction empowering quicker an ideal opportunity to-security and lessening the spread of malware.
End Point Protection Against The Threats
Firms must adopt long-lasting protection and high-security measures against the prevailing attacks and threats. Endpoint protection provides the best enterprise security solutions by providing safety against malware threats, internet traffic, and spamming, stealing, and other web threats. Moreover, it provides a high level and tight security for electronic gadgets, including PC(s), mobile phones, tablets, laptops, and VDI infrastructure protecting against stealing and losing data.
Drop Us A Line
# Erbil, Iraq: Villa No.384, G3 - Dream City
# Baghdad, Iraq: Al-Amerat Street, Al-Mansur.
# Basrah, Algeria District, near Benghazwan Hospital.
# Basrah, Algeria District, near Benghazwan Hospital.

The Power of Surveillance: Effective CCTV Solutions for Iraq
Have you ever wondered how a country facing significant security challenges can improve its safety measures? When it comes to Iraq, one technology that could make a world of difference is closed-circu...
Read More
Navigating the Digital Landscape in Iraq: Top 5 IT Solutions
Let's first think about how important IT solutions are in our lives. Imagine your life without technology. It's hard, right? IT solutions are everywhere. They make our lives easier and are really impo...
Read More
Elevating Your Business: The Advantages of Being a Gold Partner in Iraq
Elevating Your Business: The Advantages of Being a Gold Partner in Iraq
Being a Gold Partner in Iraq means occupying a privileged position that offers numerous benefits and potential for growth. Busi...
Read More