Network Penetration Testing
800+
Happy Clients
1900+
Projects Completed
30+
Business Partners
6
Countries
How to define a Network Penetration Testing?

What is our methodology?
An attack simulation carried out by our highly trained security consultants is part of our network penetration test methodology to:
• Identify environmental safety weaknesses
• Know the institution’s degree of vulnerability
• Discuss support and resolve network protection vulnerabilities found
The penetration testers at Ejaf Security Network have vast expertise in breaking the network, systems, and hosts and supporting them. They use this expertise in crucial matters to focus on the matter and provide practical guidance for remediation.
Approach
Manual Testing vs Automated
Tools
Reporting
Deliverable


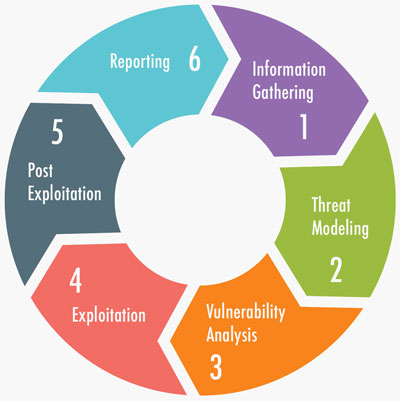
Methodology
Intelligence Gathering
Threat Modeling
Vulnerability Analysis
Exploitation
Reporting
Approach
1. Set of knowledge
2. Designing of hazard
3. Evaluation of susceptibility
2. Implementation
5. Post-implementation
6. Statistics

Intelligence Gathering
The process of collecting knowledge involves device identification, visualization of networks, banner identification and much more. Server and application exploration activities contribute to a consolidated collection of open platforms and their resources to collect as much knowledge as necessary about networks.
Initial domain footprinting, live network identification and device listing and system software and software fingerprinting involve the client and software exploration. The aim is to trace and arrange for the detection of threats jointly.
Drop Us A Line
# Basrah, Algeria District, near Benghazwan Hospital.

The Power of Surveillance: Effective CCTV Solutions for Iraq

Navigating the Digital Landscape in Iraq: Top 5 IT Solutions

