IT Security Management
Ensure the Confidentiality, Integrity,
& Availability of an Organization's Information.
800+
Happy Clients
1900+
Projects Completed
30+
Business Partners
6
Countries
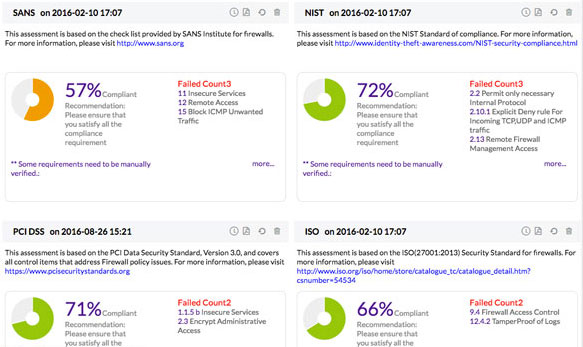
Firewall Security and Configuration Management
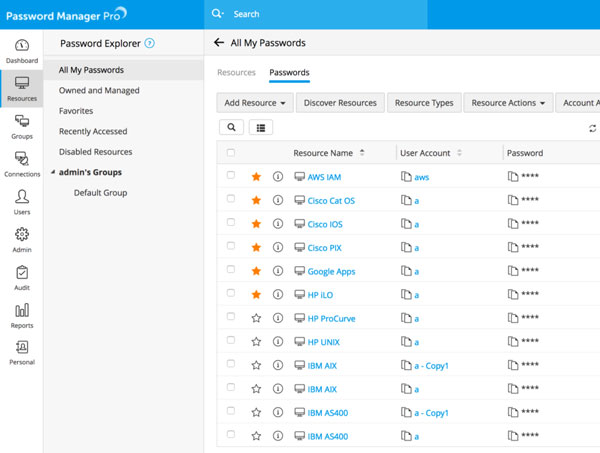
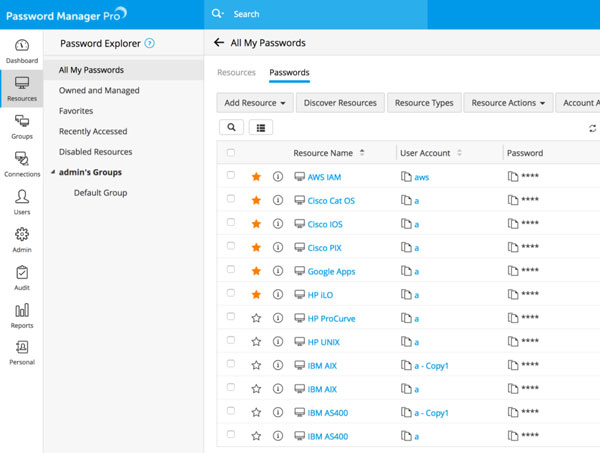
Exclusive Management Of Passwordst
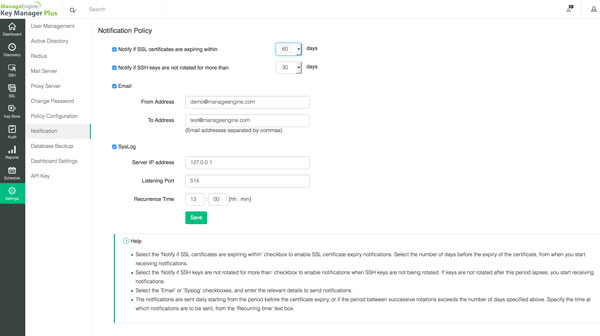
Secure Shell(SSH)Key and Secure Sockets Layer Certificate Management
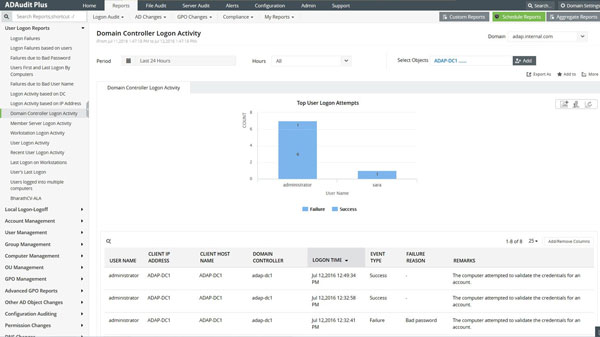
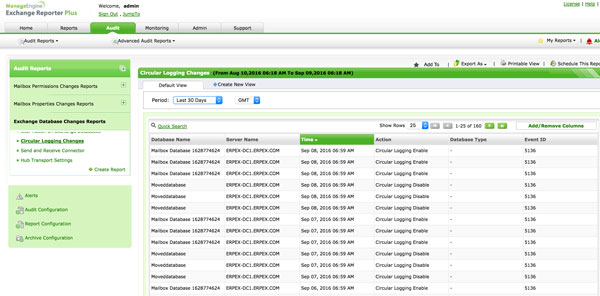
To Inspect And Report A Change in Active Directory
It is ensured that in no time, the resources, for instance, the Domain Controllers are observing, supervising, and reporting the whole information about the active directory.
Clients, team, [GPO], system, [OU], [DNS], AD Scheme, and Configuration are changed from [GUI]reports and emails.
To Inspect And Report A Change In Exchange Server
- Inspecting change, web-based, and reporting solutions are there for MS replaced environment.
- The structure and stock of smart gadgets are actively synced by the tracking and monitoring firms.
- Reports regarding outlook web access usage, mailbox traffic, and development are reported.
- It is also compatible with custom made reports in which different data filters, auto-scheduling, and different formats are used.
- It provides the inspecting tool through which you can easily inspect the unlicensed mailbox and other changes.
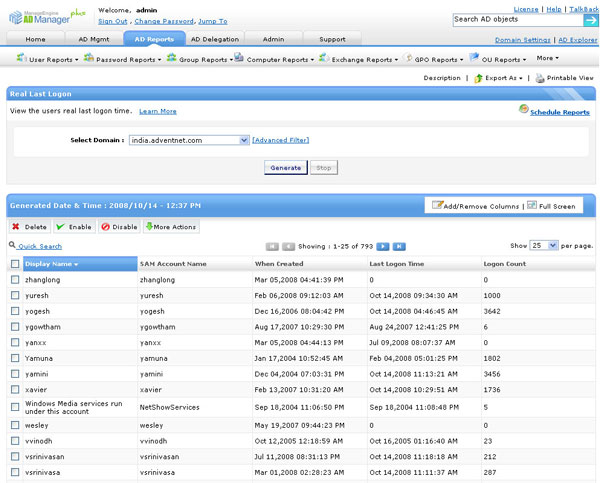
- Handling And Reporting The Active Directory:
- Web-based, active directory handler tool is provided through which you can manage your mobile phones through I phone or Android applications.
- It provides a single-comfort active directory and exchanges the executives.
- It is also compatible with templates, and a comma-separated values file user.
- It includes a huge number of reports concerning safety, Sarbanes Oxley Act—-Health-Insurance-Portability, and the act of accountability compliance or distribution reports.
- It also supports the role and OU based representative of front desk work.
- It also provides detail of user management, automated AD cleaner, and other jobs.
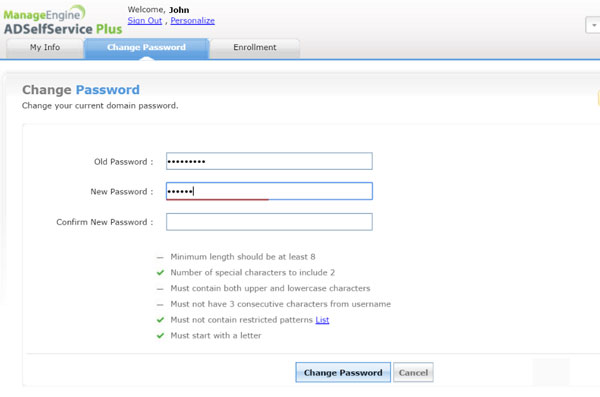
Handling of Passwords Of Active Directory
- It simplifies the passwords handling with the self-administration for valuable clients guaranteeing the high level of safety utilizing numerous word validation.
- It also applies strict password strategies on active directory. Also, on all the cloud apps.
- It automatically runs passwords at the same time on different devices so that the user won’t have to face any sort of difficulty.
- Through this, you can have coherent and flawless access to all the applications of cloud and active directory-based.
- It always informs the user about any changes, including password access or changes through emails or messages.
Active Directory Password Management
- Simplifies password management with self-service for end-users while ensuring tight security using multi-factor authentication.
- Implements granular password policies across on-premises Active Directory and cloud applications.
- Automatically synchronizes passwords to securely unify identities across multiple platforms.
- Provides seamless and secure access to cloud applications with Active Directory-based single sign-on.
- Notifies users periodically via email, SMS, and push notifications to prevent password expiration.
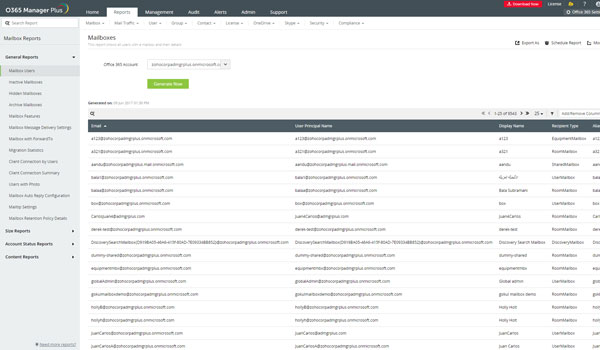
The Security And Passivity Of MicrosoftOffice-365
Network Configuration Management(NCM)
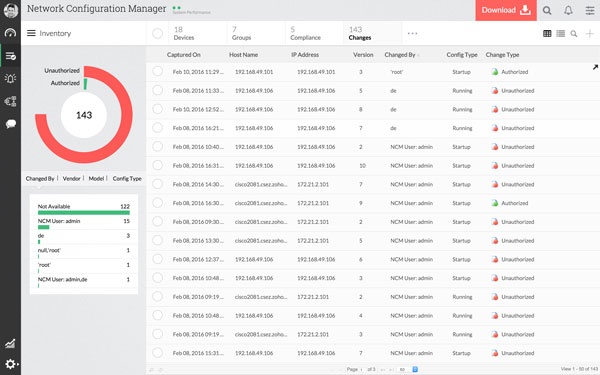
Coordinated Desktop and Mobile Device Management
Desktop Central is a coordinated desktop and cell phone handling program that helps in overseeing the servers, laptops, PC’s, cell phones, and tablets from a focal area.
Automate your normal desktop handling schedules like introducing patches, dispersing programs, dealing with your IT Assets, overseeing software licenses, checking software by using measurements, overseeing USB gadget use, assuming responsibility for remote desktop, and more integrated Desktop and Mobile Device Management.
Management Of Desktops By Microsoft SCCM

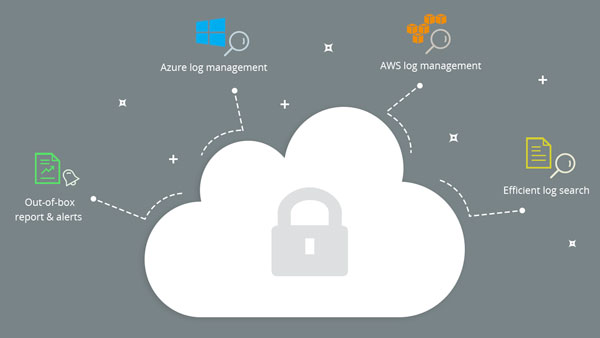
Management Of Cloud Security & Log
Information About Patch Windows, Mac, Linux, and third-party
The following are the key points about patch windows, MAC and Linux.
- Patch computers are available in networks like LAN, WAN, roaming users, and DMZ.
- Computerize the patches from recognition to categorization.
- Authorize the patches by testing it.
- They bring into play the patches of apps when they are in the stationary phase that is no one is using them
- To save time from wasting it always installs them after the business hours or office timings.
- Turns on the gadgets before its effective use and restart them automatically after the installation of patches.
- Do not categorize the patches into groups and sections.
- Inspects and then reports about the use of patches.

SIEM and The Network Threat
- SIEM solutions are provided whenever the network of firms weakens.
- They find, examine the logs from focal locations, and then provide a detailed report on it. Moreover, it also helps in archiving those logs.
- Supervises the directory environment, keeps records of all the occasions, including the client, team, _PC_, _GPO_, and _OU_ changes:
- Inspects the fileServers of windows, failover clusters, NetApp for file modifications, sharing approach, and authorization.
- Provides the client, the conditions to all the network activities to weaken the internal errors.
- Weakens the internal issues by inspecting all the networking gadgets, databases, servers of apps, and effective solutions for errors.
- Cloud security tools like Amazon web services(AWS) and Microsoft Azure that helps in keeping a record of all the events happening in cloud platforms.
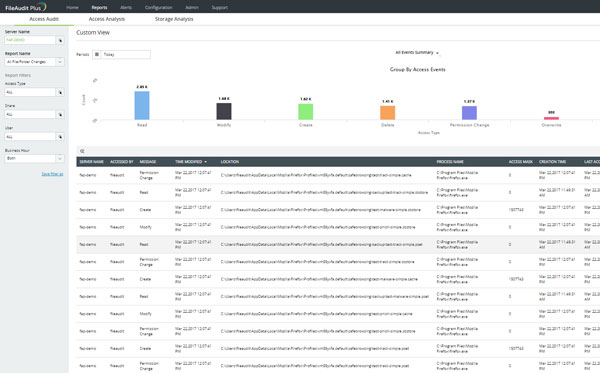
The Inspection Of File Servers And The Reporting Tools
- Web-based and real-time windows offer inspection and storage stuff through which data security is increased, information is managed effectively and fulfills the needs of compliance.
- By approaching the anomalies recording access patterns, inspecting the share, and NTFS permission, it monitors and examines the access to all folders and files.
- The storage capacity is enhanced by separating the old, unused, and unnecessary files, acquiring every bit of information about the space and the properties of files and folders.
- Remains active all the time and responds to all the violations regarding security through Email alerts.
- Agrees with [_SOX_], [_HIPAA_], [_FISMA_], [_PCI_], [_GLBA_], [_GDPR_], and other regulatory mandates.
Drop Us A Line
# Basrah, Algeria District, near Benghazwan Hospital.

The Power of Surveillance: Effective CCTV Solutions for Iraq

Navigating the Digital Landscape in Iraq: Top 5 IT Solutions

